Traffic Direction Systems (TDS)
Last weeks
we are detecting through Sonda
Ariolo a trojan infection called Keitaro TDS which redirects
HTTP request of users to malicious websites to download malware and
compromise their systems. At first glance it seems that although the
public IP is from Russia and threat intelligence engines like OTX and
virustotal don't categorize it with bad reputation or malicious IP,
when we analyze in depth, we are going to find out that it has lots
of domain name register against the same public IP. How have they
avoided to be detected by threat intelligence? Maybe with DGA,
who knows!!
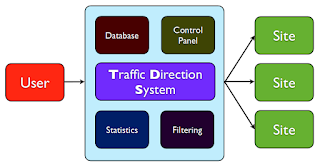
What is it
a TDS or Traffic Direction System? At the beginning it reminded me a
load balancer which can analyze the HTTP header to send the user
request to the proper web server. For instance, a mobile user with an
iPhone is redirected to the mobile web page version while an user
with a laptop is redirected to the normal web page. This is done just
looking at User-Agent attribute inside the HTTP header. But … What
is it a TDS? Actually, it is a system which can analyze users' system
settings to gather information of users like their browser, IP
address, language, Operating System, etc and TDS along with this
information and web traffic redirection techniques like server-side
redirection, iframe redirection, video redirection, etc redirect our
request to a web server.
Is this a
malicious activity? Of course it isn't, it is legal but it can be
also used for malicious activities. In fact, there are many TDS
services out there like Keitaro
TDS or WapEmpire
which help publishers and advertisers earn money with advertising
campaigns. However, these services can be also used by cybercriminals
to choose either specific targets or wide-ranging groups, depending
on their geographic locations, software preferences or language
settings to deploy and distribute malware and to steal critical
information. For instance, they can redirect users' traffic to
pharmaceutical websites in the morning and to adult websites at
night, or they can redirect unwanted traffic to default website like
Google or Yahoo and wanted traffic to pay-per-click (PPC) websites to
earn money.
How does
it work? Mainly it works with business partners or Partnerka, which
is a Russian word. On one hand, there are people who compromise
end-user systems creating a botnet from where they request legitimate
sites. On the other hand, there are people who compromise websites
injecting 0 x 0 iframes capable of handling requests from invisible
iframes. Besides, there are people who manage TDS systems to filter
and redirect traffic to make money.
Today,
this technique is also used by Black Hat SEO to make aggressive
campaigns by those who are looking for a quick financial return on
their web site. However, this trick can be banned by search engines
banning your web site.
Regards my
friend and remember, drop me a line with the first thing you are
thinking.












Commentaires
Enregistrer un commentaire