Operation Sharpshooter
I would
like to learn more and more about how latest malware work. In fact,
from time to time, I read about what are the techniques they are
using to exploit operating systems and get the information they are
looking for. I like this kind of information because I think it’s
useful for my job. Firstly, it’s useful because we are updated
about the latest vulnerabilities and this is a best practice.
Secondly, it’s useful because we can protect services better when
we know how attacks work. Finally, it’s funny and rewarding to know
how malware work.
Today, I’m
going to write about the Operation
Sharpshooter which is one of the latest malware campaign. This
operation uses the malware Rising
Sun against critical infrastructures, government and finance
such as nuclear power stations, banking, electrical companies and the
army. This malware is similar to the backdoor Duuzer
because both decode and exfiltrate the information in the same way.
Security researchers think the Operation Sharpshooter come from the
Lazarus Group.
How this
operation work? Firstly, they get lots of information about people
who work in the company they want to attack. Secondly, they send a
malicious document to victims about a new and better job. Thirdly,
victims open the malicious document which execute a shellcode. This
shellcode download the malware Rising Sun and a decoy document.
Finally, the malware get lots of information, such as operating
system, computer name, IP address, and send this information
encrypted to the control server.
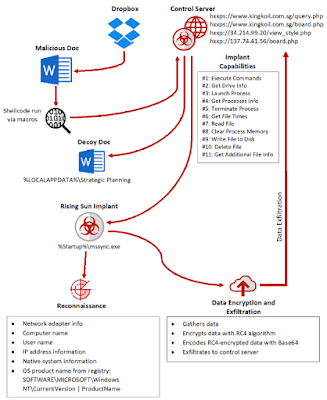 |
| Infection flow of the Rising Sun implant, which eventually sends data to the attacker’s control servers |
Actually,
I’ve seen many operations like this where social engineering and
spear phishing are the ways of inserting malware in the organization.
However, this kind of operations are increasingly persistent and
directed to some companies. Therefore, it’s more difficult to
detect these campaign. For instance, we already know about this
operation, against some critical infrastructures, but we don’t know
yet what is the goal of getting and exfiltrate this information.
Thanks for
reading my blog!! If you know books about malware, write it down in
the comments!









Commentaires
Enregistrer un commentaire