F5 AWAF - Securing APIs with BIG-IP
There are lots of web servers on the Internet and most companies know they should protect them against attacks. As a result, companies deploy WAF appliances. However, there are increasingly APIs on the Internet, which are used by apps to request and send data, that we should also protect. API servers are like web servers because they respond to requests using the HTTP protocol. Therefore, we must also protect them.
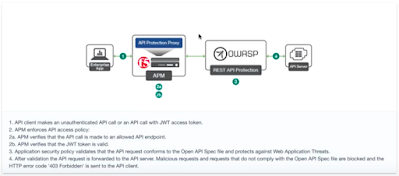
From my point of view, the API Protection feature included in APM 14.1 along with the API Security feature included in AWAF 15.0 is the best solution for protecting API servers from attackers. API Protection means authentication, authorization and federation services using OAuth, JWT, OpenID Connect or SAML while API Security means security against attacks such as SQLi, XSS or XXE. Therefore, the best way to protect API servers will be to import an OpenAPI Spec 2.0 file into BIG-IP which will add the details of the API such as paths, API servers, responses, API protection profile, etc.
REST API Security - Configuration example
Configuring a WAF policy to protect API servers is really easy. Firstly, we should deploy the AWAF module (formerly ASM module). Secondly, we have to create a security policy where we are going to choose API Security as Policy Template. In addition, we are going to import the OpenAPI file where application-specific configuration is defined such as URLs, parameters and methods. Finally, we have to assign the security policy to the virtual server where the API service is listening. Once the security policy is created, we can see a list of allowed components in the security policy.
The API Security template is great because F5 AWAF is going to configure a security policy to protect API services easily for us. However, we can add more security layers to this protection. For instance, I like to add a bot defense profile to prevent all types of malicious bots from accessing the API services. This protection relies on signatures and javascript based challenges. Therefore, it is important to highlight that JS challenges need to be used with caution.
There is another security layer I really like to add to web assets such as API servers. As attackers can send legitimate requests at a high scale, they can bring down an API service. As a result, I like to add a DDoS Defense profile to API servers. There are mainly three protection mechanisms. Firstly, transaction per second (TPS) Based DoS Defense which is the most straightforward mechanism because it measures requests rate. Secondly, the stress-based mechanism is similar to TPS but it only mitigates when the protected asset is under stress. Finally, behavioral anomaly detection (BADoS) mechanism which uses a machine learning algorithm.
To sum up, if you have API services, you will also have to protect them. If you have F5 AWAF, you have almost everything. You only have to enable API Security to your services.
Regards my friends! Do you protect your API servers?












Commentaires
Enregistrer un commentaire