F5 BIG-IP APM – Identity-aware proxy (IAP)
I’ve been reading about Identity-Aware Proxy (IAP) this week because it’s a new feature in F5 BIG-IP APM and I wanted to know exactly what the advantages of this solution are. Initially, I was reading and I didn’t understand anything. It were the same as I knew it. Authentication, Single Sign-On (SSO) and a few more things. However, I’ve realised it’s a new feature from the point of view of usability. It’s a new feature for deploying a Zero Trust model validation based on granular context- and identity-awareness, securing every application access request.
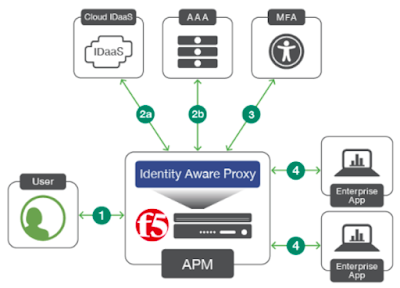
Identity Aware Proxy (IAP) delivers secure access to applications based on the principle of “Never Trust, Always Verify”. It means, IAP is a Zero Trust architecture where there is no a secure network perimeter and there is no trusted insider. As a result, everything is untrusted, even users that have already been authenticated, authorized, and granted access to applications and resources. IAP should verify not just at the time a user requests access but also when users have access to the application or resource, and upon every subsequent access request and attempt.
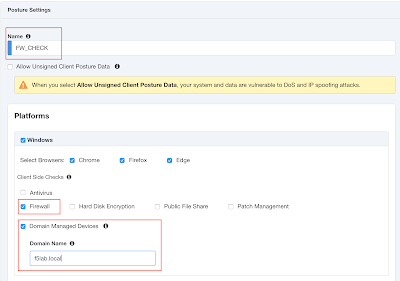
IAP grants access to applications by evaluating real-time device posture, user identity and step-up authentication. Thanks to F5 Access Guard, IAP can check the device security posture such as firewall, antivirus, patches, etc from the client-side. Therefore, IAP along with Access Guard go beyond simply checking device integrity at authentication. Instead, they deliver continuous, ongoing device posture checks. As a result, if IAP detects any change in the device integrity, it may either limit or stop the user’s application access.
Define a firewall Posture Assessment
IAP is going to authenticate, authorize and encrypt every access request. We can also add an extra security layer with MFA as well as enable SSO. IAP supports modern authentication and authorization protocols like SAML, OpenID Connect and OAuth. In addition, due to every access request is encrypted, we can use IAP instead of VPN to access the enterprise network because IAP is per request application access while VPNs apply session-based access. Therefore, IAP is more secure than VPNs.
BIG-IP APM is a single, centralized control point for securing and managing user access to applications, wherever they may be hosted
Thanks to Access Guided Configuration (AGC) for version 15 and Simplified Guided Configuration (SGC) for version 16, it is really easy to deploy an IAP architecture. There is a step by step guide where we can easily configure the device security posture, the authentication servers, SSO authentication profiles, etc. It’s the best way to deploy an IAP solution with a Zero Trust model validation.
Access Guided Configuration - Single Proxy
To sum up, I knew most of the features about F5 BIG-IP APM such as Identity federation, MFA, SSO, SSL VPN and API Protection but I didn’t know the Identity-aware proxy (IAP) solution very well until recently. Once I’ve been reading about it, I’m going to take the plunge and I’m going to configure a small lab to see how it is working with the AGC. I think this is the best way to know how IAP works.
Regards my friends! What have you been doing this Christmas?













Commentaires
Enregistrer un commentaire